How cybercriminals are exploiting the pandemic
The pandemic has created new opportunities for cybercriminals to attack individuals, institutions, and infrastructure. Here's how we can fight back.
Ellen Rowe (ER) is a Foreign Cybersecurity Policy Analyst at the Federal Government of Canada. She is currently a graduate student at the Max Bell School of Public Policy where she serves as Vice President External Affairs at the Public Policy Association of Graduate Students (PPAGS). Views are her own. Write us at newsletterthebell@gmail.com
THE RECENT RANSOMWARE ATTACK THAT CRIPPLED the Colonial Pipeline in the United States underscores the ways in which vulnerabilities in critical infrastructure can be exploited. The pipeline is now back online, but if a ransomware attack had targeted Canada’s health infrastructure, would we have been able to recover as quickly?
According to experts, Canada's health system is under siege from cybercriminals trying to access patient information and other data. These criminals are pulling out all the stops in an attempt to make a quick buck or two. Since the start of the pandemic, reported cybercrimes have increased 300 percent while ransom demands have tripled, costing victims an average of $312,000 per attack. Whether you work at home or in the office, cyber attack techniques such as phishing, malware, and ransomware remain a huge threat. These attacks highlight that cyber security awareness campaigns are more important than ever -- but more should also be done beyond campaigns.
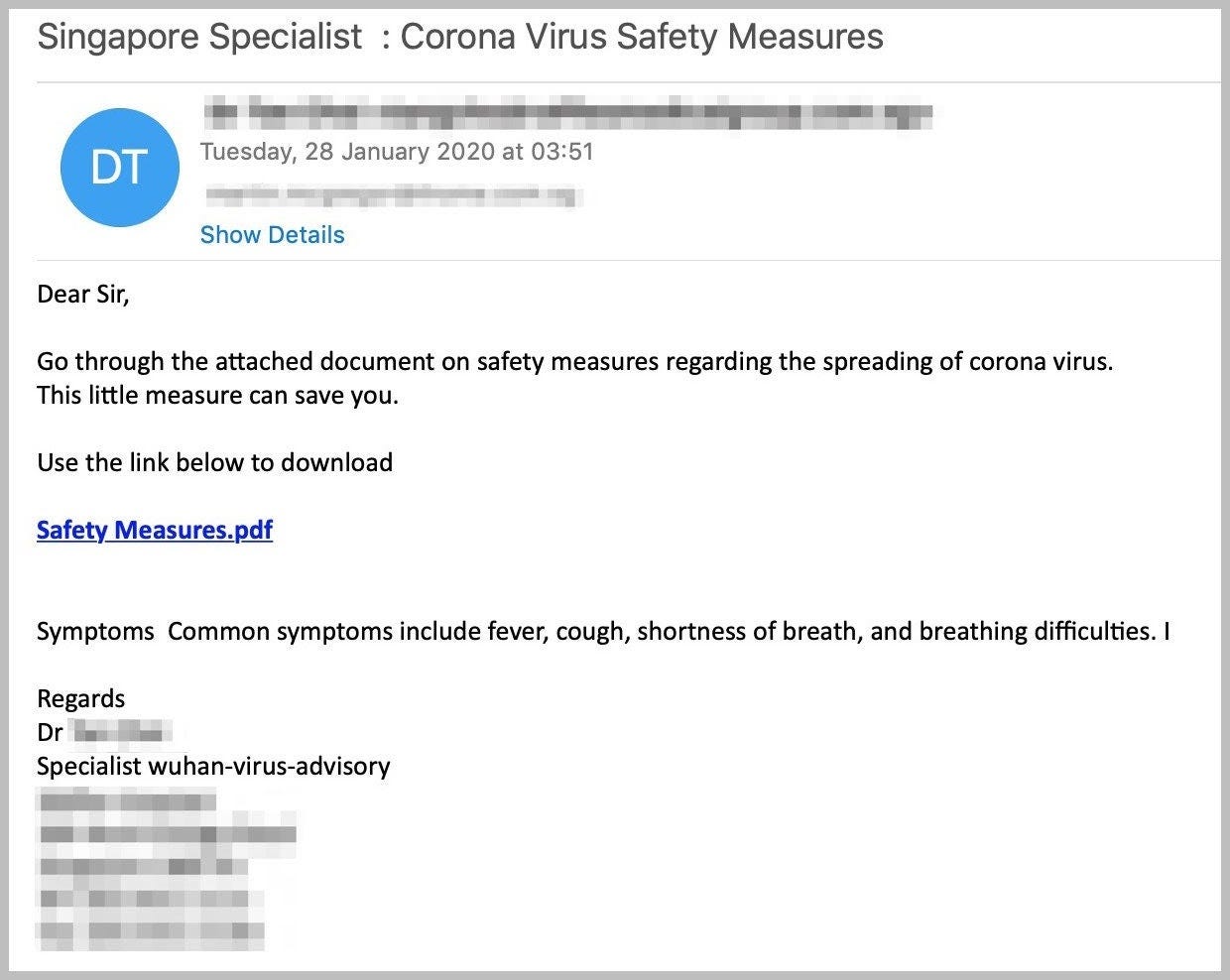
Whether that email you just received focuses on coronavirus safety measures or booking vaccination appointments, cybercriminals “deploy manipulative attacks intended to strike certain emotions to cause end users to skip critical thinking and go straight for that detrimental click.” These manipulative attacks over email are better known as “phishing attacks,” where attackers are fishing for any and all kinds of information. Traditionally, individuals receive a phishing email from a well-known source directing them to click on a link or download an attachment that then asks for personal information and account details, typically for financial gain. Cybercriminals will use the information provided “to impersonate the victim and apply for credit cards or loans, open bank accounts, and other fraudulent activity.”
Source: Wired
In a more targeted approach, spear phishing (personalised phishing) has become popular among criminals. Individuals are waiting around the world en masse to receive news on booking vaccination appointments, making them susceptible to these personalized attacks. For example, as vaccines are prepared to be shipped around the globe, hackers have attempted to disrupt the supply chain through spear-phishing emails. Prior to shipping the vaccine, the first targeted company fell prey to a criminal impersonating an employee at Haier Biomedical. Since staff had anticipated receiving an email from Haier, many executives and managers promptly provided their username and passwords as requested in the pdf attachment. IBM Security later discovered that this attack was directed at a total of 44 companies in 14 countries globally. In order to reduce internal vulnerabilities, companies should implement cyber security education programs. By educating staff on the tell-tale signs of phishing emails, the risk of future attacks can be lessened.
Similar to phishing attacks over email or text messages, phishing websites lure in individuals who are looking for information on a particular topic. As of May 5, 2021, the US Attorney’s Office alongside Homeland Security Investigations seized the malicious website Freevaccinecovax.org, now blocked and unavailable to the public. The website was a fake biotech company that claimed to be manufacturing vaccines. Visitors to the site were asked to provide their hometown city and “apply for information by downloading a PDF file to their computers.” By using official logos from the World Health Organization (WHO) and Pfizer, the malicious website appeared as official as any other.
More recently, smishing (mobile phishing), vishing (voice phishing) and malvertising (malicious code in advertisements) have become the newest cyber attack techniques. Luckily, attackers rarely review for spelling errors, incomplete url links, and incorrect logos, raising user suspicion and decreasing the effectiveness of these scam techniques. Unfortunately, the relatively high sophistication levels of malware attacks are not as easy to detect.
Cyber criminals continue to push the boundaries by replicating websites and deploying malware to disrupt information systems. Last year, criminals maliciously replicated the Johns Hopkins University Global COVID-19 Cartographic Map.
Cybercriminals were able to lure people looking for more information on COVID-19 cases to what looked like the legitimate John Hopkins’ COVID-19 Map. From there, visitors were prompted to download an application that would enhance the features of the interactive map. In the back end however, malicious files began to compromise the victim’s computer, stealing “cookies, browsing histories, user IDs, passwords, and even cryptocurrency keys.”
Then in early May, the Colonial Pipeline, which provides fuel to the east coast of the United States, was shut down due to a ransomware attack. In contrast to phishing which gains access to personal information to then access funds, ransomware denies access to personal information or systems and requests a payment (ransom) to gain access back to it. As explained by the public security expert Christian Leuprecht, ransomware is “a big game-changer because we always felt that we can keep our critical infrastructure reasonably safe and the bad guys can go after other countries. But this attack shows the deterrents aren’t working.” Cyber criminals gain access to health care services, municipal websites, and vaccine testing facilities by cracking simple passwords and sending phishing emails with malicious attachments and links.
These examples show that criminals are using increasingly sophisticated techniques to gain access to individuals and organizations, to steal personal information, and make a profit. Similar to physical threats, we need to be more aware of these dangers, and set up sufficient protections in our personal and professional lives.
Moving forward, education programs and awareness campaigns such as the Canadian Centre for Cyber Security’s (CCCS) annual Get Cyber Safe national public campaign and the Cyber Security Awareness Month every October must continue, especially as new techniques are constantly being deployed. In addition to existing government cyber security protocols, individuals and organizations should be diligent in following good cyber hygiene. These include, but are not limited to, regular password updates, frequent vulnerability checks, software updates, and data backups, and the use of multi-factor authentication (MFA). Policymakers should also establish cyber security frameworks based on layered vigilance, readiness and resilience. Although there is no one solution to completely eliminate cyber attacks, mitigating the risks against Canada’s health infrastructure is a step in the right direction. (ER)
For more information on cyber security, make sure to check out the Cyber Centre Learning Hub at https://www.cyber.gc.ca/en/. Also, if you receive a suspicious email referencing COVID-19, you can report it to ec.sectiec-ecitsec.ec@canada.ca or the CCCS at cyberincident@cyber.gc.ca.
Watch: Blow your mind with this scale model of the solar system, built in the Nevada desert.
Listen: Exorcise your angst with Michael Beach’s new album Dream Violence.
Social: Check out who is a doctor:
___
The Bell is edited by Emily Nickerson, Mariel Aramburu, and Andrew Potter of the Max Bell School of Public Policy at McGill University. If you have any feedback or would like to contribute to this newsletter, please send an email to the editors at newsletterthebell@gmail.com